传统方式的购买 TLS 证书,流程繁琐, 采购周期长。 vault 的优点在于 Vault PKI allows users to dynamically generate X.509 certificates quickly and on demand. Vault PKI can streamline distributing TLS certificates and allows users to create PKI certificates with a single command. Vault PKI reduces overhead around the usual manual process of generating a private key and CSR, submitting to a CA, and waiting for a verification and signing process to complete, while additionally providing an authentication and authorization mechanism to validate as well.
为什么需要 TLS 为了避免被中间人劫持:
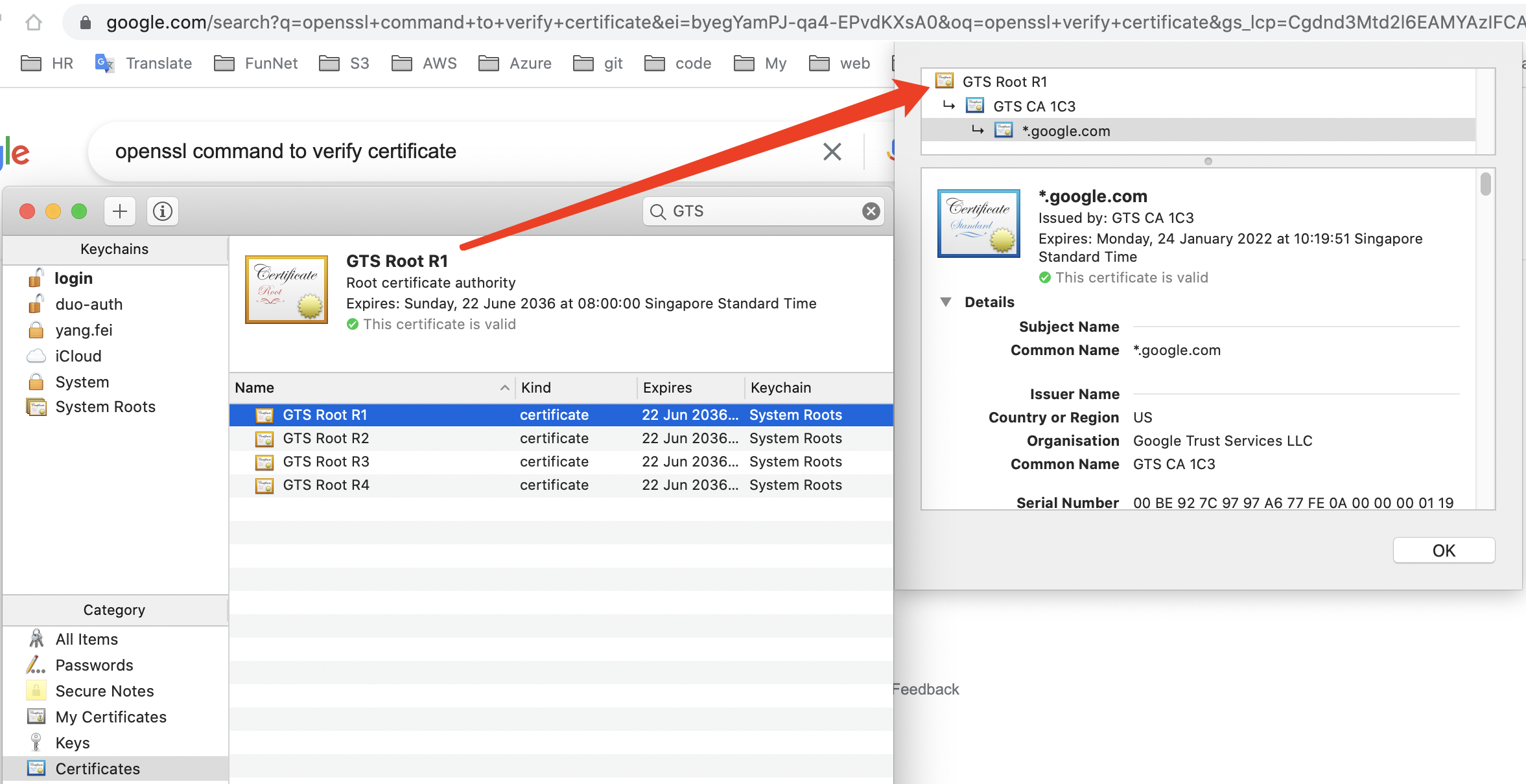
安全传输公钥: 权威机构的公钥不需要传输,因为权威机构会和主流的浏览器或操作系统合作,将他们的公钥内置在浏览器或操作系统环境中。客户端收到证书之后,只需要从证书中找到权威机构的信息,并从本地环境中找到权威机构的公钥,就能正确解密A公钥。
保证客户端收到的证书是服务器下发的证书,没有被中间人篡改过。文章一 , 文章二 或者自行 Google
举例 当我们访问的 Google 的时候,我们的电脑内置了权威机构的根证书 GTS Root。由此根证书,我们可以验证谷歌站点发过来的 ca chain 真实性。
vault pki 参考:
搭建 vault 可以参考我的另外一篇 post vault 实践
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 # Creating the root CA: # First, enable the pki secrets engine at the pki path: $ vault secrets enable pki # Tune the pki secrets engine to issue certificates with a maximum time-to-live (TTL) # of 87600 hours (10 years): $ vault secrets tune -max-lease-ttl=87600h pki # Generate the root CA, extracting the root CA's certificate to root.crt; the secret # key is not exported! $ vault write -field=certificate pki/root/generate/internal common_name="feiyang.com" \ ttl=87600h > root.crt # This generates a new self-signed CA certificate and private key. Vault will automatically # revoke the generated root at the end of its lease period (TTL); the CA certificate will # sign its own Certificate Revocation List (CRL). # Configure the CA and CRL URLs: $ vault write pki/config/urls \ issuing_certificates="$VAULT_ADDR/v1/pki/ca" \ crl_distribution_points="$VAULT_ADDR/v1/pki/crl" # Creating the intermediate CA: # First, enable the pki secrets engine at the pki_int path: $ vault secrets enable -path=pki_int pki # Tune the pki_int secrets engine to issue certificates with a maximum time-to-live (TTL) # of 43800 hours (5 years): $ vault secrets tune -max-lease-ttl=43800h pki_int # Execute the following command to generate an intermediate and save the CSR as # pki_intermediate.csr: $ vault write -format=json pki_int/intermediate/generate/exported \ common_name="feiyang.com Intermediate Authority" ttl="43800h" format="pem" > pki_intermediate # Extract the private key & certificate signing request from the previous command' s output:$ jq -r '.data.private_key' < pki_intermediate > intermediate.key.pem $ jq -r '.data.csr' < pki_intermediate > pki_intermediate.csr # Sign the intermediate certificate with the root certificate and save the generated # certificate as intermediate.cert.pem: $ vault write -format=json pki/root/sign-intermediate csr=@pki_intermediate.csr \ format="pem" \ | jq -r '.data.certificate' > intermediate.cert.pem # Once the CSR is signed and the root CA returns a certificate, it can be imported back # into Vault: $ vault write pki_int/intermediate/set-signed certificate=@intermediate.cert.pem
然后就是拼接成 ca chain (颁发的证书在前,CA证书在后)
1 2 3 4 5 6 $ cat intermediate.cert.pem > intermediate.chain.pem$ cat root.crt >> intermediate.chain.pemroot@ubuntu18-108:/etc/vault.d/pki_test# ls feiyang.txt intermediate.chain.pem pki_intermediate root.crt intermediate.cert.pem intermediate.key.pem pki_intermediate.csr
为 client 创建一个 role, client 端可以用来申请证书。
1 2 3 4 5 6 vault write pki_int/roles/feiyang-dot-com \ allowed_domains="feiyang.com" \ allow_subdomains=true \ max_ttl="720h" vault write pki_int/issue/feiyang-dot-com common_name="test.feiyang.com" ttl="24h" >>feiyang.txt
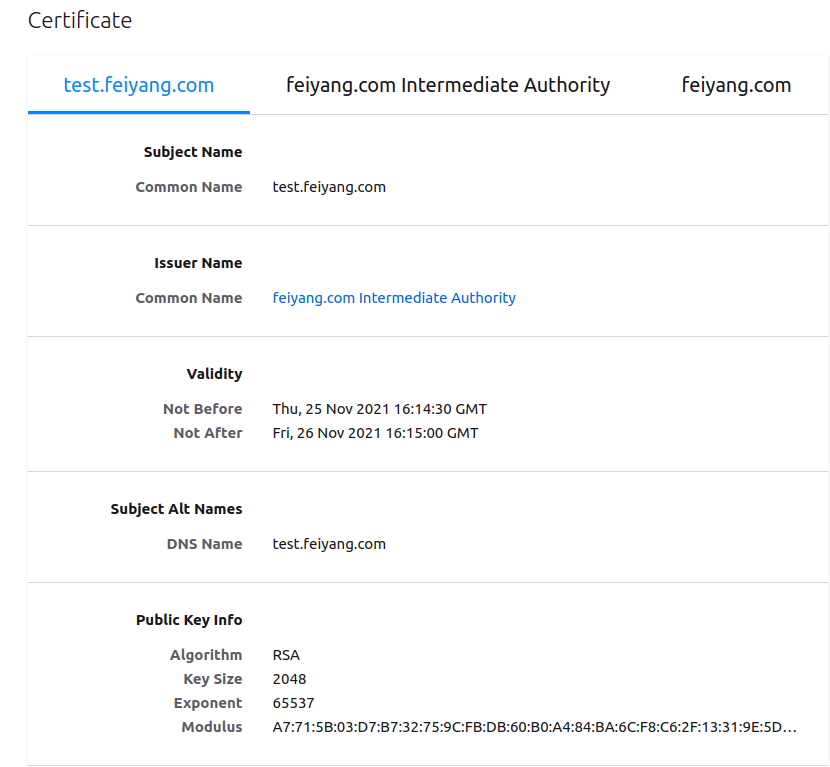
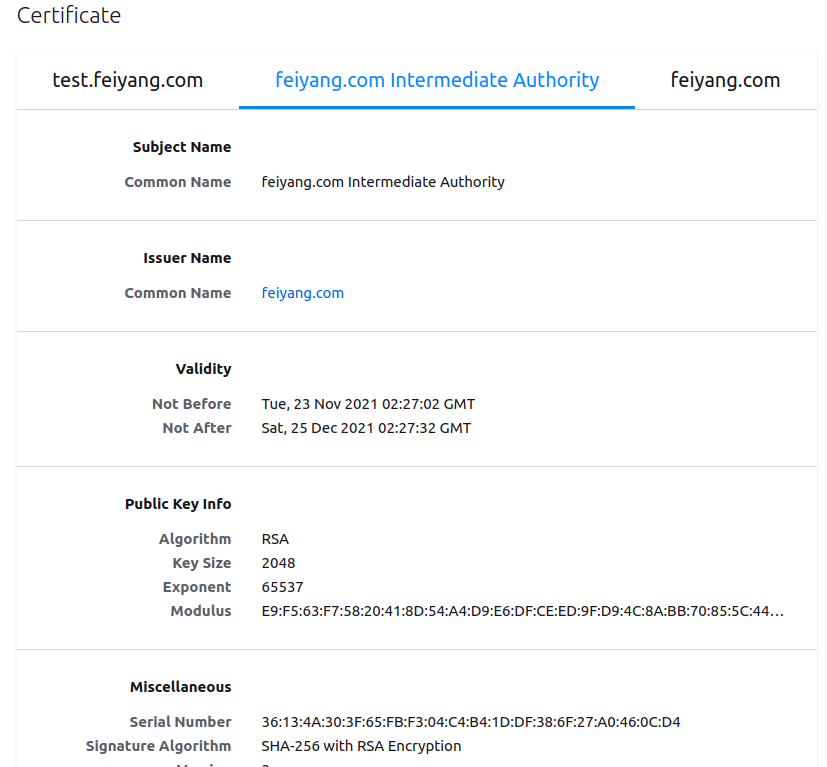
我们来看一下, 返回的 test.feiyang.com 有什么
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 root@ubuntu18-108:/etc/vault.d/pki_test# cat feiyang.txt Key Value --- ----- ca_chain [-----BEGIN CERTIFICATE----- MIIDrDCCApSgAwIBAgIUNhNKMD9l+/MExLQd3zhvJ6BGDNQwDQYJKoZIhvcNAQEL BQAwFjEUMBIGA1UEAxMLZmVpeWFuZy5jb20wHhcNMjExMTIzMDIyNzAyWhcNMjEx MjI1MDIyNzMyWjAtMSswKQYDVQQDEyJmZWl5YW5nLmNvbSBJbnRlcm1lZGlhdGUg QXV0aG9yaXR5MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6fVj91gg QY1UpNnm387tn9lMirtwhVxEexXPJHL00St3J+io7gbTkw6DNZE5wwsoILqB4jKe rGsWsk2zIZlebISBzPVhIdLqeVyTW0/hUtLc4KoHgcrAtI8qwaqtGMAOmLWBLHdZ Gb6j2uiuf6773YPkNT0zaemD/t3JndFFCzZne3xUsOkPUrODmtHUAENHPAxuDQhP DIYNDENi9KRvh5CD778gXFYgoh+MuWHx8+vcy8IJi/ykfR9yE+P2beP/N/11Jm02 uALJJ0NeQ/nGDaktR4Q5SgkmLY8rwgWRWQmJBR7welSY/ZjPfjfdlmeGdHecYPK9 acGBKk/81lryOQIDAQABo4HaMIHXMA4GA1UdDwEB/wQEAwIBBjAPBgNVHRMBAf8E BTADAQH/MB0GA1UdDgQWBBRIhaij4GVicVWQAcZvTOxdPg4F5jAfBgNVHSMEGDAW gBSPMN9+BzUlsMkk8Hv+GVDS0nD3gjA+BggrBgEFBQcBAQQyMDAwLgYIKwYBBQUH MAKGImh0dHA6Ly8xOTIuMTY4LjY0LjM6ODIwMC92MS9wa2kvY2EwNAYDVR0fBC0w KzApoCegJYYjaHR0cDovLzE5Mi4xNjguNjQuMzo4MjAwL3YxL3BraS9jcmwwDQYJ KoZIhvcNAQELBQADggEBAEVNSisWlg+TdPct9VXKJ6cLsHdWNzIfIXk3lFNzcd1J zWuYEtBYpAvdLFAy3KzmmepTP/jqKN6+nw4JDOMzv/kaRx0Fyoq/uvBu3GILH3NB ZjMWkOCuvEdFozKj9qTj4GkL9wFzUfEra0w6x+2tr1qodCtcjxxHUv9/jr0slFle e/zOsLpNd/q+ozWNmt2KEN3STCugIoMhlvAQESUtiESbphMoqPFVw1cc5SX8LI78 cQMgEyT67wiH9KHsJfcJQexzQCQUJcebXbO9HvUTnP94kdVZIN3uDot5OiDWJPqg M8uwej97SAyjjnjGR8bkO+Ct1SuSDV5URP2E/9possg= -----END CERTIFICATE-----] certificate -----BEGIN CERTIFICATE----- MIIDZjCCAk6gAwIBAgIUQu0BTkmbJHjwUGiXDjLOX47ki18wDQYJKoZIhvcNAQEL BQAwLTErMCkGA1UEAxMiZmVpeWFuZy5jb20gSW50ZXJtZWRpYXRlIEF1dGhvcml0 eTAeFw0yMTExMjUxNjE0MzBaFw0yMTExMjYxNjE1MDBaMBsxGTAXBgNVBAMTEHRl c3QuZmVpeWFuZy5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCn cVsD17cydZz722CwpIS6bPjGLxMxnl2xk2yfGdhQZc2z/GEtyQd028n6PwPoxJ9U 6dwGZcyzS/iHTZhmThv6hvy2QZgeIbWB8n58Cnf7ExWmwmplUVQd549NP9RwFtuN tBKZjxpVyPiwp3dVoBuA+3rVBo4z5Cfz1HQ0b53j5Vb9AjNX8VrDFWOpGOF2LWPg nZOWLQaCMMOd7iuXjPKLJtO2VDbBGBYOx0YXhyr5itQDhM8UKgEVU1kJZgna7CWu CfBdQh+new+YgsPTQx4zkca472Uyb9rykTxzRfnly0b5WkhwDoyvCMPZtFerf3T7 LjJhqnVWcCgA1R0sb0/HAgMBAAGjgY8wgYwwDgYDVR0PAQH/BAQDAgOoMB0GA1Ud JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAdBgNVHQ4EFgQUSjt1XbgoJdJceVB+ VP5bMuGFEnAwHwYDVR0jBBgwFoAUSIWoo+BlYnFVkAHGb0zsXT4OBeYwGwYDVR0R BBQwEoIQdGVzdC5mZWl5YW5nLmNvbTANBgkqhkiG9w0BAQsFAAOCAQEAdTP2kqpS P1qTmt/ILAuJ5wz6Fe+78v3uv5PjAGz4CJ4gcdqVXqVxn0a6PPi3VuCg2y50h/zC a/T7OWC/Qcu3No0Puad2T2osVbrH/pf/WvmieMnwPcc+8Ay8pgEDO1iP8R7m/YB4 fnt1x2ePkeHRp984QnCt19a8nVNTnD5bsGR4dIcchgz0xDyGlro7rDY8MppBJZNy 24Dg6BJOo+GTFwO3+lvoB4RrlVQpr74a5y4PJJnRdwq5ov/1qMd5E1MkzJAdPPhs xi5+oaa7Ja9hpYk9iZUcdZrePE31WTkqnNZvkC+DZGQ3eZbdO/uK2fRYvX4tjOyX 16kYe2YkPN9KzA== -----END CERTIFICATE----- expiration 1637943300 issuing_ca -----BEGIN CERTIFICATE----- MIIDrDCCApSgAwIBAgIUNhNKMD9l+/MExLQd3zhvJ6BGDNQwDQYJKoZIhvcNAQEL BQAwFjEUMBIGA1UEAxMLZmVpeWFuZy5jb20wHhcNMjExMTIzMDIyNzAyWhcNMjEx MjI1MDIyNzMyWjAtMSswKQYDVQQDEyJmZWl5YW5nLmNvbSBJbnRlcm1lZGlhdGUg QXV0aG9yaXR5MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6fVj91gg QY1UpNnm387tn9lMirtwhVxEexXPJHL00St3J+io7gbTkw6DNZE5wwsoILqB4jKe rGsWsk2zIZlebISBzPVhIdLqeVyTW0/hUtLc4KoHgcrAtI8qwaqtGMAOmLWBLHdZ Gb6j2uiuf6773YPkNT0zaemD/t3JndFFCzZne3xUsOkPUrODmtHUAENHPAxuDQhP DIYNDENi9KRvh5CD778gXFYgoh+MuWHx8+vcy8IJi/ykfR9yE+P2beP/N/11Jm02 uALJJ0NeQ/nGDaktR4Q5SgkmLY8rwgWRWQmJBR7welSY/ZjPfjfdlmeGdHecYPK9 acGBKk/81lryOQIDAQABo4HaMIHXMA4GA1UdDwEB/wQEAwIBBjAPBgNVHRMBAf8E BTADAQH/MB0GA1UdDgQWBBRIhaij4GVicVWQAcZvTOxdPg4F5jAfBgNVHSMEGDAW gBSPMN9+BzUlsMkk8Hv+GVDS0nD3gjA+BggrBgEFBQcBAQQyMDAwLgYIKwYBBQUH MAKGImh0dHA6Ly8xOTIuMTY4LjY0LjM6ODIwMC92MS9wa2kvY2EwNAYDVR0fBC0w KzApoCegJYYjaHR0cDovLzE5Mi4xNjguNjQuMzo4MjAwL3YxL3BraS9jcmwwDQYJ KoZIhvcNAQELBQADggEBAEVNSisWlg+TdPct9VXKJ6cLsHdWNzIfIXk3lFNzcd1J zWuYEtBYpAvdLFAy3KzmmepTP/jqKN6+nw4JDOMzv/kaRx0Fyoq/uvBu3GILH3NB ZjMWkOCuvEdFozKj9qTj4GkL9wFzUfEra0w6x+2tr1qodCtcjxxHUv9/jr0slFle e/zOsLpNd/q+ozWNmt2KEN3STCugIoMhlvAQESUtiESbphMoqPFVw1cc5SX8LI78 cQMgEyT67wiH9KHsJfcJQexzQCQUJcebXbO9HvUTnP94kdVZIN3uDot5OiDWJPqg M8uwej97SAyjjnjGR8bkO+Ct1SuSDV5URP2E/9possg= -----END CERTIFICATE----- private_key -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAp3FbA9e3MnWc+9tgsKSEumz4xi8TMZ5dsZNsnxnYUGXNs/xh LckHdNvJ+j8D6MSfVOncBmXMs0v4h02YZk4b+ob8tkGYHiG1gfJ+fAp3+xMVpsJq ZVFUHeePTT/UcBbbjbQSmY8aVcj4sKd3VaAbgPt61QaOM+Qn89R0NG+d4+VW/QIz V/FawxVjqRjhdi1j4J2Tli0GgjDDne4rl4zyiybTtlQ2wRgWDsdGF4cq+YrUA4TP FCoBFVNZCWYJ2uwlrgnwXUIfp3sPmILD00MeM5HGuO9lMm/a8pE8c0X55ctG+VpI cA6MrwjD2bRXq390+y4yYap1VnAoANUdLG9PxwIDAQABAoIBAB5H9bnALTVG59j0 V4wadJZyVpsgsEvs4+zVSHONbP09K/I81iY9kMelZ+WFt+NEi7wDfvL5Pge+2Xc+ pSz7OzwXZWRggG4Skoypmg48pm4ViXja9/rStm+iDNxfir+qopIB2stCgfS5n5/y 6TXm+pJc6F3WDal8vWzvIwTImrk32WgNa3TxA/KtkawbhiAwOsvT4S5SlQmsgpFK EtC+lmbx9aZTeoAcor/XMz9hbk0pB3r9VK4Z4MxOz5WrNcb2wPZ81EuVVBBdEYCI auaNTnLl8r5w/VMSTi2DvSuZ9SC6yGc4Gv8Y3GvsHpxujAQlls3kqJQtPAPs4Cwg hNS8JyECgYEAwDrhkaW7AUhrhQ5655Vv4/EF5sFNIPp8A0e7jzq7iDSmbvdG1EGU eaUYqj7zY6USRf2B2cnTYo7WQJedshK6/mRErFv+prsNUT0kyKIgEKgLWPMZwzAQ 6RI9uDRiRYNbcLlU8Wukxt1A+9JlddVFfwI0L98J9v6TkgRXL8ZTKM0CgYEA3v1s J6ZdjjBqA1+qzSEkmHjSk9CPTNuQ4/sIciOXdcu8r+g9fbj88I4ZrT4q8L7Xqojj bgB/mJpebRrkLOGU8iBCqCHjJSqciBBU1c2v8quoLOD4Mo2naBLqI2ge30RJGxEY Yt8Bacmlr3q2SsDZ6GtLQf7UVCfN+3u+Gd4CquMCgYBYFeMtSYNSyCu00fjRy/F0 wwpQPj2oof9XxXQV4vTyKiYl7RvAwbhWsaeGw8fl3ktsVQk+kjRSEl/tQ0yYv+p+ DdZGIPWk00v78Qe9BEWrPEXO4b7paUomcxxjH2X0soehNNvOsOPV2KchfbzObQcm dw0Q7qRzUR6wJ1sIYlnS9QKBgQDPCftOgSAiMf9sbHnYhapFywCxb5ZtpPtNQbog x70MCQODTB0zyvtGmplqiesype72Dq0jaGEQHlwH70zmAvjZKmzZUMVmr76wcoFi Fd0Ecq7uJF8uCOnjLpSoFTd80xkRgXjj6+yS/T/RwxzYIWDxdBVnDCS2klKk6cqi l8hgQwKBgQCCG+QMKA6o6gtYnxdi6S3EF3Mo0b9MB3r4OFRFHN7Sk1ICxWB5oy94 YSER0HMxcl+N6COfr4QiA46Me0ixEJ/CXnE9ey7zrvojchLbtIZrZPenhAiFxiiC /wDATARa8QuQ2HrBt7G/zzCujWQilbGcWWqK/K/4ESA40Ib4N05grQ== -----END RSA PRIVATE KEY----- private_key_type rsa serial_number 42:ed:01:4e:49:9b:24:78:f0:50:68:97:0e:32:ce:5f:8e:e4:8b:5f
verify in nginx 安装 Nginx 的过程就省略了,只看设置
nginx server 这里的 server.crt 就是 ca chain, 把 feiyang.txt 里面的 certificate 和 issuing_ca 拼接起来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 server { listen 443 ssl http2; listen [::]:443 ssl http2; server_name test.feiyang.com; root /usr/share/nginx/html; ssl_certificate "/etc/pki/nginx/server.crt"; ssl_certificate_key "/etc/pki/nginx/private/server.key"; ssl_session_cache shared:SSL:1m; ssl_session_timeout 10m; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on; [root@centos7 nginx]# cat /etc/pki/nginx/server.crt -----BEGIN CERTIFICATE----- MIIDZjCCAk6gAwIBAgIUQu0BTkmbJHjwUGiXDjLOX47ki18wDQYJKoZIhvcNAQEL BQAwLTErMCkGA1UEAxMiZmVpeWFuZy5jb20gSW50ZXJtZWRpYXRlIEF1dGhvcml0 eTAeFw0yMTExMjUxNjE0MzBaFw0yMTExMjYxNjE1MDBaMBsxGTAXBgNVBAMTEHRl c3QuZmVpeWFuZy5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCn cVsD17cydZz722CwpIS6bPjGLxMxnl2xk2yfGdhQZc2z/GEtyQd028n6PwPoxJ9U 6dwGZcyzS/iHTZhmThv6hvy2QZgeIbWB8n58Cnf7ExWmwmplUVQd549NP9RwFtuN tBKZjxpVyPiwp3dVoBuA+3rVBo4z5Cfz1HQ0b53j5Vb9AjNX8VrDFWOpGOF2LWPg nZOWLQaCMMOd7iuXjPKLJtO2VDbBGBYOx0YXhyr5itQDhM8UKgEVU1kJZgna7CWu CfBdQh+new+YgsPTQx4zkca472Uyb9rykTxzRfnly0b5WkhwDoyvCMPZtFerf3T7 LjJhqnVWcCgA1R0sb0/HAgMBAAGjgY8wgYwwDgYDVR0PAQH/BAQDAgOoMB0GA1Ud JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAdBgNVHQ4EFgQUSjt1XbgoJdJceVB+ VP5bMuGFEnAwHwYDVR0jBBgwFoAUSIWoo+BlYnFVkAHGb0zsXT4OBeYwGwYDVR0R BBQwEoIQdGVzdC5mZWl5YW5nLmNvbTANBgkqhkiG9w0BAQsFAAOCAQEAdTP2kqpS P1qTmt/ILAuJ5wz6Fe+78v3uv5PjAGz4CJ4gcdqVXqVxn0a6PPi3VuCg2y50h/zC a/T7OWC/Qcu3No0Puad2T2osVbrH/pf/WvmieMnwPcc+8Ay8pgEDO1iP8R7m/YB4 fnt1x2ePkeHRp984QnCt19a8nVNTnD5bsGR4dIcchgz0xDyGlro7rDY8MppBJZNy 24Dg6BJOo+GTFwO3+lvoB4RrlVQpr74a5y4PJJnRdwq5ov/1qMd5E1MkzJAdPPhs xi5+oaa7Ja9hpYk9iZUcdZrePE31WTkqnNZvkC+DZGQ3eZbdO/uK2fRYvX4tjOyX 16kYe2YkPN9KzA== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDrDCCApSgAwIBAgIUNhNKMD9l+/MExLQd3zhvJ6BGDNQwDQYJKoZIhvcNAQEL BQAwFjEUMBIGA1UEAxMLZmVpeWFuZy5jb20wHhcNMjExMTIzMDIyNzAyWhcNMjEx MjI1MDIyNzMyWjAtMSswKQYDVQQDEyJmZWl5YW5nLmNvbSBJbnRlcm1lZGlhdGUg QXV0aG9yaXR5MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6fVj91gg QY1UpNnm387tn9lMirtwhVxEexXPJHL00St3J+io7gbTkw6DNZE5wwsoILqB4jKe rGsWsk2zIZlebISBzPVhIdLqeVyTW0/hUtLc4KoHgcrAtI8qwaqtGMAOmLWBLHdZ Gb6j2uiuf6773YPkNT0zaemD/t3JndFFCzZne3xUsOkPUrODmtHUAENHPAxuDQhP DIYNDENi9KRvh5CD778gXFYgoh+MuWHx8+vcy8IJi/ykfR9yE+P2beP/N/11Jm02 uALJJ0NeQ/nGDaktR4Q5SgkmLY8rwgWRWQmJBR7welSY/ZjPfjfdlmeGdHecYPK9 acGBKk/81lryOQIDAQABo4HaMIHXMA4GA1UdDwEB/wQEAwIBBjAPBgNVHRMBAf8E BTADAQH/MB0GA1UdDgQWBBRIhaij4GVicVWQAcZvTOxdPg4F5jAfBgNVHSMEGDAW gBSPMN9+BzUlsMkk8Hv+GVDS0nD3gjA+BggrBgEFBQcBAQQyMDAwLgYIKwYBBQUH MAKGImh0dHA6Ly8xOTIuMTY4LjY0LjM6ODIwMC92MS9wa2kvY2EwNAYDVR0fBC0w KzApoCegJYYjaHR0cDovLzE5Mi4xNjguNjQuMzo4MjAwL3YxL3BraS9jcmwwDQYJ KoZIhvcNAQELBQADggEBAEVNSisWlg+TdPct9VXKJ6cLsHdWNzIfIXk3lFNzcd1J zWuYEtBYpAvdLFAy3KzmmepTP/jqKN6+nw4JDOMzv/kaRx0Fyoq/uvBu3GILH3NB ZjMWkOCuvEdFozKj9qTj4GkL9wFzUfEra0w6x+2tr1qodCtcjxxHUv9/jr0slFle e/zOsLpNd/q+ozWNmt2KEN3STCugIoMhlvAQESUtiESbphMoqPFVw1cc5SX8LI78 cQMgEyT67wiH9KHsJfcJQexzQCQUJcebXbO9HvUTnP94kdVZIN3uDot5OiDWJPqg M8uwej97SAyjjnjGR8bkO+Ct1SuSDV5URP2E/9possg= -----END CERTIFICATE----- [root@centos7 nginx]# cat /etc/pki/nginx/private/server.key -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAp3FbA9e3MnWc+9tgsKSEumz4xi8TMZ5dsZNsnxnYUGXNs/xh LckHdNvJ+j8D6MSfVOncBmXMs0v4h02YZk4b+ob8tkGYHiG1gfJ+fAp3+xMVpsJq ZVFUHeePTT/UcBbbjbQSmY8aVcj4sKd3VaAbgPt61QaOM+Qn89R0NG+d4+VW/QIz V/FawxVjqRjhdi1j4J2Tli0GgjDDne4rl4zyiybTtlQ2wRgWDsdGF4cq+YrUA4TP FCoBFVNZCWYJ2uwlrgnwXUIfp3sPmILD00MeM5HGuO9lMm/a8pE8c0X55ctG+VpI cA6MrwjD2bRXq390+y4yYap1VnAoANUdLG9PxwIDAQABAoIBAB5H9bnALTVG59j0 V4wadJZyVpsgsEvs4+zVSHONbP09K/I81iY9kMelZ+WFt+NEi7wDfvL5Pge+2Xc+ pSz7OzwXZWRggG4Skoypmg48pm4ViXja9/rStm+iDNxfir+qopIB2stCgfS5n5/y 6TXm+pJc6F3WDal8vWzvIwTImrk32WgNa3TxA/KtkawbhiAwOsvT4S5SlQmsgpFK EtC+lmbx9aZTeoAcor/XMz9hbk0pB3r9VK4Z4MxOz5WrNcb2wPZ81EuVVBBdEYCI auaNTnLl8r5w/VMSTi2DvSuZ9SC6yGc4Gv8Y3GvsHpxujAQlls3kqJQtPAPs4Cwg hNS8JyECgYEAwDrhkaW7AUhrhQ5655Vv4/EF5sFNIPp8A0e7jzq7iDSmbvdG1EGU eaUYqj7zY6USRf2B2cnTYo7WQJedshK6/mRErFv+prsNUT0kyKIgEKgLWPMZwzAQ 6RI9uDRiRYNbcLlU8Wukxt1A+9JlddVFfwI0L98J9v6TkgRXL8ZTKM0CgYEA3v1s J6ZdjjBqA1+qzSEkmHjSk9CPTNuQ4/sIciOXdcu8r+g9fbj88I4ZrT4q8L7Xqojj bgB/mJpebRrkLOGU8iBCqCHjJSqciBBU1c2v8quoLOD4Mo2naBLqI2ge30RJGxEY Yt8Bacmlr3q2SsDZ6GtLQf7UVCfN+3u+Gd4CquMCgYBYFeMtSYNSyCu00fjRy/F0 wwpQPj2oof9XxXQV4vTyKiYl7RvAwbhWsaeGw8fl3ktsVQk+kjRSEl/tQ0yYv+p+ DdZGIPWk00v78Qe9BEWrPEXO4b7paUomcxxjH2X0soehNNvOsOPV2KchfbzObQcm dw0Q7qRzUR6wJ1sIYlnS9QKBgQDPCftOgSAiMf9sbHnYhapFywCxb5ZtpPtNQbog x70MCQODTB0zyvtGmplqiesype72Dq0jaGEQHlwH70zmAvjZKmzZUMVmr76wcoFi Fd0Ecq7uJF8uCOnjLpSoFTd80xkRgXjj6+yS/T/RwxzYIWDxdBVnDCS2klKk6cqi l8hgQwKBgQCCG+QMKA6o6gtYnxdi6S3EF3Mo0b9MB3r4OFRFHN7Sk1ICxWB5oy94 YSER0HMxcl+N6COfr4QiA46Me0ixEJ/CXnE9ey7zrvojchLbtIZrZPenhAiFxiiC /wDATARa8QuQ2HrBt7G/zzCujWQilbGcWWqK/K/4ESA40Ib4N05grQ== -----END RSA PRIVATE KEY-----
ubuntu20 verify 需要先把根证书 root.crt 导入 ubuntu20, 这里我们 copy & paste Adding a self-signed certificate to the “trusted list”
1 2 3 4 5 # sudo cp root.crt /usr/local/share/ca-certificates/ vim /usr/local/share/ca-certificates/feiyang.crt sudo update-ca-certificates echo "192.168.64.4 test.feiyang.com" >> /etc/hosts
添加好证书后,我们就可以用 curl 测试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 root@ubuntu20:/usr/local/share/ca-certificates# curl -v https://test.feiyang.com * Trying 192.168.64.4:443... * TCP_NODELAY set * Connected to test.feiyang.com (192.168.64.4) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/certs/ca-certificates.crt CApath: /etc/ssl/certs * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384 * ALPN, server accepted to use h2 * Server certificate: * subject: CN=test.feiyang.com * start date: Nov 25 16:14:30 2021 GMT * expire date: Nov 26 16:15:00 2021 GMT * subjectAltName: host "test.feiyang.com" matched cert's "test.feiyang.com" * issuer: CN=feiyang.com Intermediate Authority * SSL certificate verify ok. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 * Using Stream ID: 1 (easy handle 0x563b3aa8be10) > GET / HTTP/2 > Host: test.feiyang.com > user-agent: curl/7.68.0 > accept: */* > * Connection state changed (MAX_CONCURRENT_STREAMS == 128)! < HTTP/2 200 < server: nginx/1.20.1 < date: Fri, 26 Nov 2021 02:48:04 GMT < content-type: text/html < content-length: 4833 < last-modified: Fri, 16 May 2014 15:12:48 GMT < etag: "53762af0-12e1" < accept-ranges: bytes
ubuntu18 firefox 我们把证书导入到另外一台 Ubuntu 桌面版,浏览器 firefox 里面。参考 Get Firefox to trust your self signed certificates
1 echo "192.168.64.4 test.feiyang.com" >> /etc/hosts
vault revoke 1 2 3 4 5 root@ubuntu18-108:/etc/vault.d/pki_test# vault write pki_int/revoke serial_number=42:ed:01:4e:49:9b:24:78:f0:50:68:97:0e:32:ce:5f:8e:e4:8b:5f Key Value --- ----- revocation_time 1637895959 revocation_time_rfc3339 2021-11-26T03:05:59.165880864Z